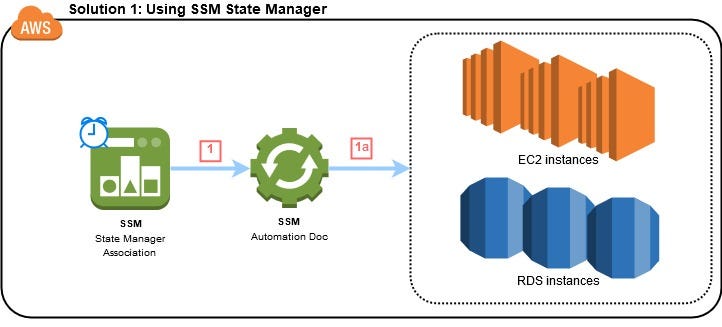
Introduction:
In the realm of cloud computing, cost optimization reigns supreme. Within the vast ecosystem of AWS, where resources are provisioned and billed on a pay-as-you-go basis, maximizing efficiency becomes paramount. One significant area for potential savings lies in the management of EC2 and RDS instances. Not every instance needs to run incessantly; often, non-production instances or those not serving round-the-clock operations can be safely halted to reduce costs.
However, manually starting and stopping instances on a daily basis can be a tedious and error-prone task for cloud users. This is where automation steps in, offering a streamlined solution to manage instance lifecycle efficiently. AWS System Manager’s State Manager provides a robust framework for automating such tasks, ensuring instances are active precisely when needed.
Creating IAM Role and Policy:
To empower System Manager with the necessary permissions, a dedicated IAM role and policy must be configured. Lets create a IAM policy with name StopStartInstancePolicy encompassing actions like describing, starting, stopping, and rebooting EC2 and RDS instances, grants System Manager the requisite authority over resources
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:Describe*",
"ec2:Start*",
"ec2:Stop*",
"ec2:Reboot*",
"rds:Describe*",
"rds:Start*",
"rds:Stop*",
"rds:Reboot*"
],
"Resource": "*"
}
]
}
Now lets create a IAM Role with name StopStartInstanceRole with a custom trust policy allowing System Manager (ssm.amazonaws.com) to assume the role and attach the above created policy.
Trust Relationship:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ssm.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
Setting Up State Manager Association:
With permissions in place, State Manager associations are configured to orchestrate instance start and stop workflows. Utilizing the “AWS-StartEC2Instance” and “AWS-StopEC2Instance” documents, associations are defined to trigger instance actions based on a specified schedule.
For starting instances, create an association named “StartInstances”, defining a schedule using a CRON schedule builder. This association triggers the “AWS-StartEC2Instance” document, initiating instance start operations at the specified time.
AWS System Manager -> Node Management -> State Manager
Create Association:
Name(Provide a name for your Association): StartInstances
Document: AWS-StartEC2Instance
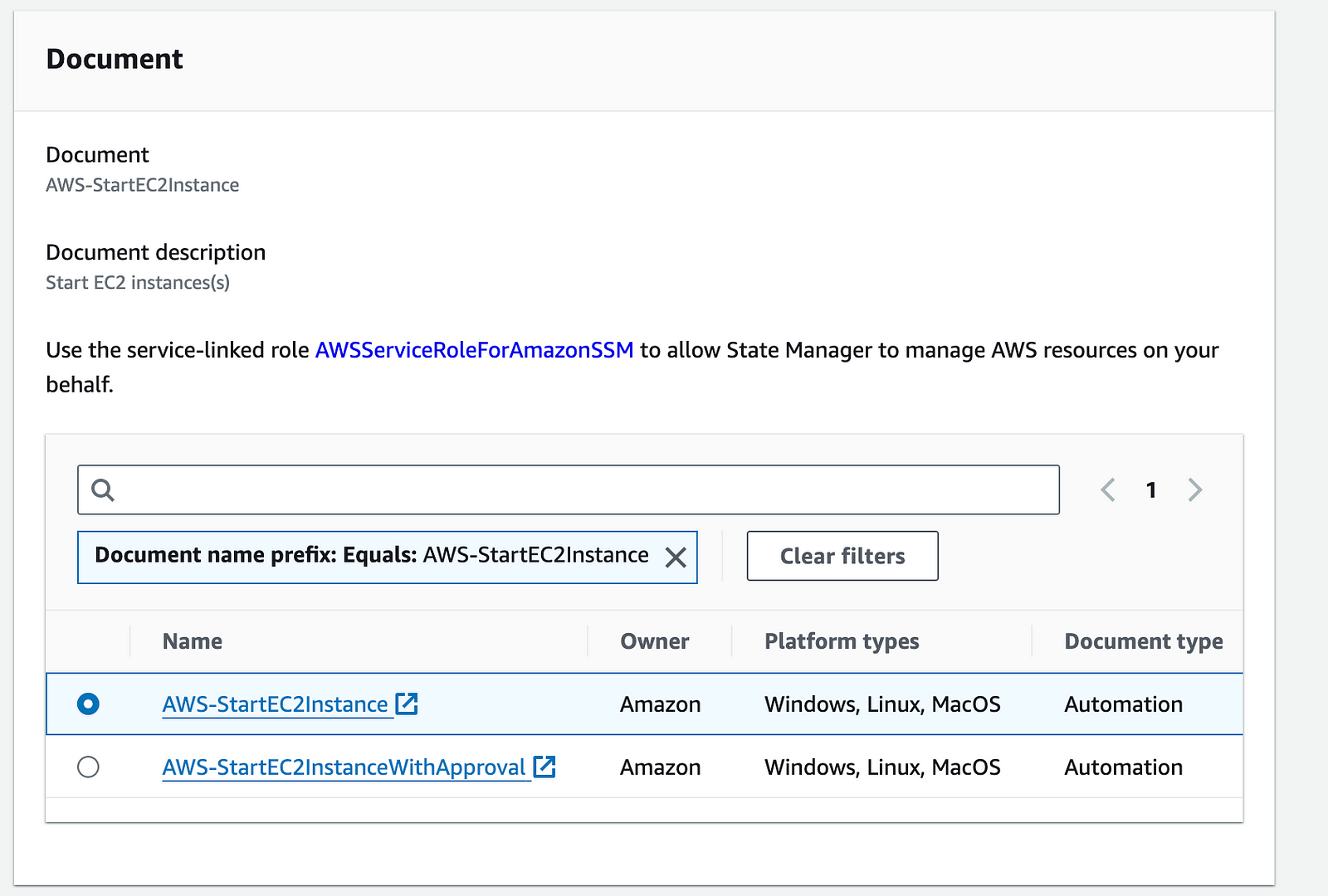
Input parameters: InstanceId -> Enable Show interactive instance picker -> Show all instances -> Select the instance
AutomationAssumeRole: Add the role created above
Specify schedule: On Schedule
CRON schedule builder: Daily
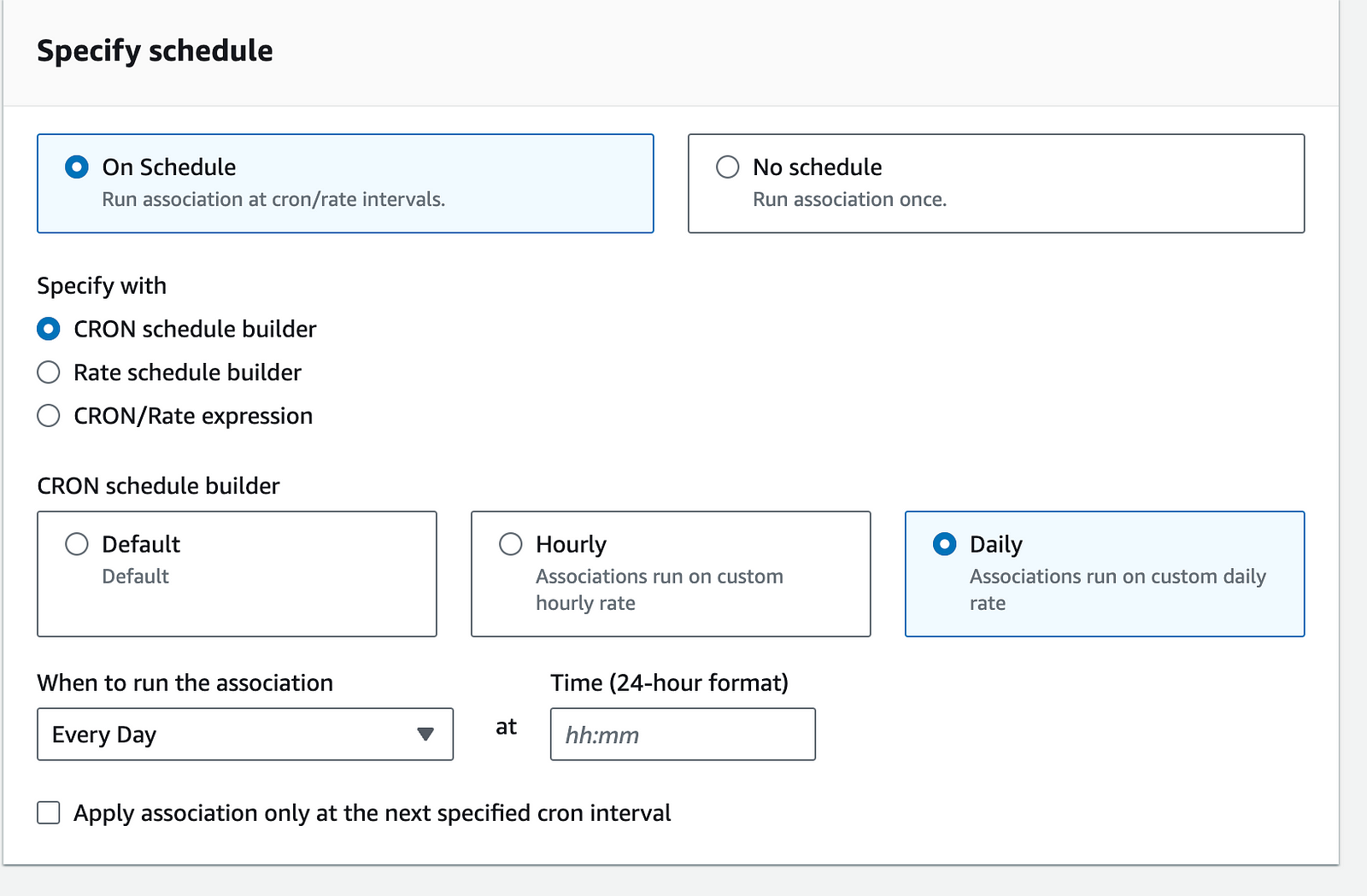
Add time to start the instance
If you want to skip the cron for first run select
Apply association only at the next specified cron interval
Similarly, for stopping instances, followed the same process, creating an association named “StopInstances” and employing the “AWS-StopEC2Instance” document. This association halts instances according to the configured schedule, ensuring resources are inactive during non-operational hours.
Conclusion:
By leveraging System Manager’s State Manager, AWS users can automate the start and stop lifecycle of EC2 instances, optimizing costs without sacrificing operational efficiency. Through a carefully orchestrated setup involving IAM roles, policies, and State Manager associations, the burden of manual instance management is alleviated, enabling organizations to focus on core business objectives while maximizing the value derived from AWS services.

